Cybersecurity fundamentals: securing your digital life
Cybersecurity fundamentals encompass vital practices like using strong passwords, enabling two-factor authentication, and regularly updating software to protect against cyber threats.
Cybersecurity fundamentals are crucial in today’s digital age. Have you ever thought about what it takes to keep your online presence secure? In this article, we will dive into essential concepts and practices that help safeguard your information.
Understanding cybersecurity fundamentals
Understanding cybersecurity fundamentals is crucial for anyone navigating the digital world today. It helps individuals protect their personal information and understand the risks associated with online activities. The foundation of cybersecurity includes key concepts that everyone should know.
Key Concepts in Cybersecurity
Cybersecurity is not just about using complicated software or having technical knowledge. It’s about adopting certain behaviors and understanding principles that can keep both individual and organizational data safe. Here are some essential concepts:
-
🎯 Attack Vectors: Ways that attackers can gain unauthorized access to a system.
-
⚠️ Threats: Potential dangers that could exploit vulnerabilities in a system.
-
🛠️ Vulnerabilities: Weaknesses in a system that can be targeted by attackers.
-
🛡️ Defense Strategies: Measures taken to protect systems from threats.
Another key idea is the importance of awareness and education in cybersecurity. Being knowledgeable about potential threats can improve your defenses. Regular training and updates on the latest security practices can go a long way in keeping information safe.
Network security is also a fundamental aspect. This involves securing the hardware and software technologies used in networking. It includes protecting both the organizational network and individual devices from malicious attacks. Firewalls, intrusion detection systems, and secure Wi-Fi connections all contribute to strong network security.
Common Cyber Threats
Understanding common threats helps to prepare against them. Here are a few:
- Phishing: A technique where attackers try to trick individuals into sharing personal information.
- Malware: Software designed to harm or exploit any programmable device.
- Ransomware: A type of malware that blocks access to files until a ransom is paid.
Lastly, creating a culture of security within organizations cannot be overstated. Everyone in the organization should feel responsible for maintaining security protocols. This culture improves overall security awareness and reduces risks significantly.
Importance of strong passwords
The importance of strong passwords cannot be overstated in the world of cybersecurity. A strong password acts as the first line of defense against unauthorized access to your accounts. This simple step can significantly lower the chances of falling victim to cyber attacks.
Characteristics of Strong Passwords
A strong password should be complex and unique. Ideally, it should contain a mix of uppercase and lowercase letters, numbers, and symbols. Here are some key characteristics:
-
🔒 At least 12 characters long
-
🔢 Includes a combination of letters, numbers, and special characters
-
🚫 Avoids common words or sequences like “123456” or “password”
It’s also important to avoid using personal information in your passwords, such as birthdays or names, as these can be easily guessed or found online. Instead, consider using a passphrase—a sequence of random words that create a memorable but secure password.
Benefits of Strong Passwords
Using strong passwords offers several advantages. They not only protect your personal and financial information but also enhance overall internet security. Some benefits include:
- Reduces the risk of account hacking
- Helps prevent identity theft
- Gives you peace of mind when browsing online
Regularly updating your passwords is another essential practice. Even strong passwords can become compromised over time, especially if data breaches occur. Changing your passwords every few months and using different passwords for different accounts can create an additional layer of security.
Lastly, consider using a password manager to keep track of your unique passwords. These tools can generate strong passwords and store them securely, making it easier for you to maintain your online security without having to remember every password.
Common cyber threats and how to recognize them
Common cyber threats pose significant risks to individuals and organizations alike. Recognizing these threats is crucial for maintaining your online safety and security. Being aware of potential dangers can help you take proactive measures to protect your sensitive information.
Types of Cyber Threats
There are various types of cyber threats that you may encounter. Understanding these can help sharpen your instincts when browsing online. Here are some of the most common:
-
🎣 Phishing: This involves attackers sending fake emails or messages to trick you into revealing personal information, such as passwords or credit card numbers.
-
💻 Malware: A broad term for malicious software, malware is designed to disrupt, damage, or gain unauthorized access to computer systems.
-
💸 Ransomware: This type of malware locks your files and demands a ransom for their release. It’s important to back up your data to protect against this threat.
Additionally, social engineering is often used by attackers. This method involves manipulating individuals into breaking security protocols or sharing sensitive information. Always be cautious about unexpected requests for personal data.
How to Recognize Cyber Threats
Recognizing cyber threats can be challenging, but there are warning signs to look out for. For example, be wary of:
- Unrecognized emails, especially those asking for sensitive information.
- Unexpected software installations on your devices.
- Unusual account activity, such as login attempts from unfamiliar locations.
Another important tactic is to pay attention to the URLs of websites you visit. Many phishing sites will have slightly altered URLs that may look legitimate at first glance. Always check for secure connections indicated by “https” at the beginning of the URL.
Cultivating a habit of skepticism while browsing online can go a long way in protecting yourself. Make it a practice to verify sources before clicking on links or downloading files. This way, you can significantly reduce your risk of falling prey to cyber threats.
Best practices for online safety
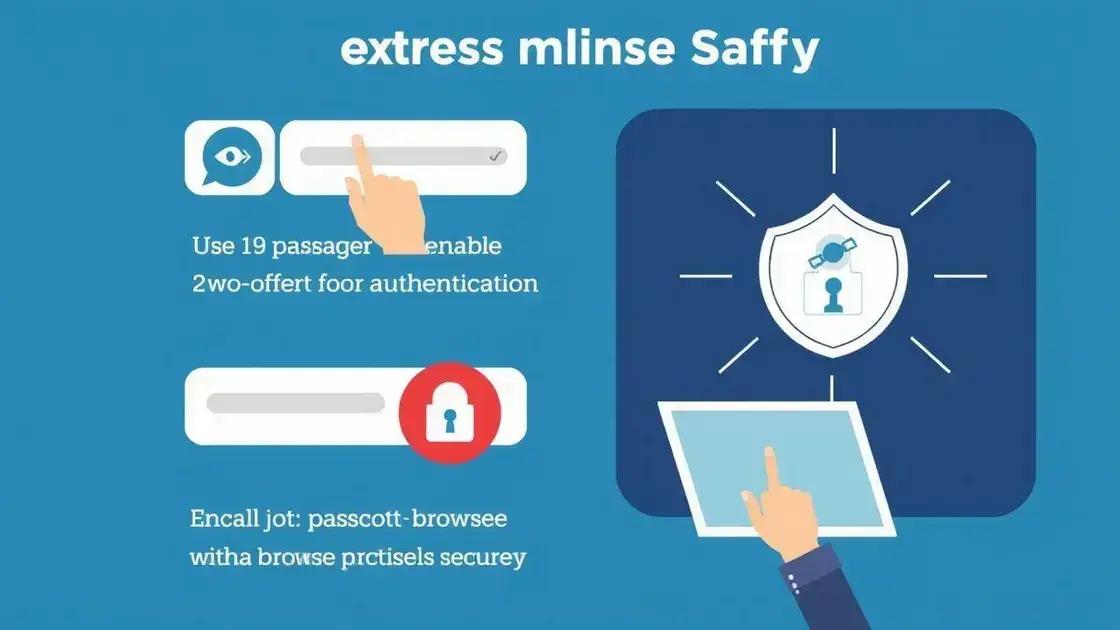
Implementing the best practices for online safety is essential for protecting your personal information and maintaining your digital privacy. By adopting these practices, you can create a safer browsing experience and significantly reduce your risk of becoming a target for cyber threats.
Use Strong and Unique Passwords
One of the fundamental steps towards online safety is using strong and unique passwords for each of your accounts. A password should consist of at least 12 characters, including a mix of letters, numbers, and special symbols. Avoid using personal information that others could easily guess, like birthdays or names.
Enable Two-Factor Authentication
Another important practice is to enable two-factor authentication (2FA) whenever possible. This extra layer of security requires not only your password but also a second form of identification, such as a text message code or authentication app. 2FA significantly decreases the likelihood of unauthorized access to your accounts.
Keep Software Up to Date
Keeping your software and devices up to date is crucial for protecting against vulnerabilities that hackers can exploit. Regularly check for updates on your operating system, browsers, and applications. Enable automatic updates if possible, so you always have the latest security features.
Be Aware of Phishing Attacks
Awareness of phishing attacks is vital for online safety. Be cautious of unsolicited emails, especially those requesting personal information or prompting you to click a link. Verify the source before providing any details or responding to messages. Look for signs such as poor grammar, generic greetings, or misspelled domain names.
Use Secure Connections
Whenever possible, ensure you are using secure connections by checking for “https://” in the URL before entering sensitive information. Avoid using public Wi-Fi networks for transactions or accessing sensitive accounts. If necessary, consider using a virtual private network (VPN) to encrypt your connection.
In summary, being proactive about online safety helps protect your personal data and enhances your digital experience. By following these best practices, you can keep yourself safer from cyber threats and create a healthier online environment.
Role of antivirus software
The role of antivirus software is vital in the fight against cyber threats. This software helps protect your devices from malicious attacks that can compromise your personal information and disrupt your digital life. Understanding how antivirus programs work can empower you to improve your overall cybersecurity.
How Antivirus Software Works
Antivirus software operates by scanning your system for known threats. It uses a combination of techniques to detect and eliminate malware, including:
-
📝 Signature-Based Detection: This method relies on a database of known malware signatures. The antivirus scans files and compares them to this database to find matches.
-
🕵️♂️ Heuristic Analysis: Heuristic detection looks for suspicious behavior or characteristics associated with malware, even if the malware hasn’t been formally identified yet.
-
⚙️ Behavioral Detection: This technique monitors programs while they run to identify any unusual actions that could indicate a malware infection.
By utilizing these methods, antivirus software can effectively guard against a wide array of threats like viruses, worms, spyware, and ransomware.
Importance of Regular Updates
It’s crucial to keep your antivirus software updated to ensure that you are protected against the latest threats. Cybercriminals are constantly developing new malware, and regular updates add the latest signatures and defenses to your software. Without these updates, your antivirus could become less effective over time.
Choosing the Right Antivirus Solution
When selecting antivirus software, consider factors such as ease of use, compatibility with your devices, and the level of customer support provided. Look for software that offers comprehensive features, including:
- Real-time scanning: Constant monitoring for threats as they arise.
- Web protection: Blocking unsafe websites and downloads.
- System performance impact: Minimal slowdowns while running.
No single solution can guarantee complete protection, but having a reliable antivirus program significantly reduces your risk of malware infections. Regularly check and adjust your security settings to enhance your defense further.
How to secure your home network
Securing your home network is essential for protecting your devices and personal information. With the rise of smart devices, having a secure network helps prevent unauthorized access and cyber threats. By following these guidelines, you can enhance your home network’s security.
Change Default Settings
Most routers come with default usernames and passwords that are easy for hackers to guess. Change these settings immediately to something unique. Use a strong password that combines letters, numbers, and special characters.
Enable WPA3 Encryption
Ensure that your router is set to use the latest security protocol, which is usually WPA3. This encryption standard provides better security than older protocols like WEP and WPA2. If your router doesn’t support WPA3, use WPA2 and update your router firmware regularly.
Use a Guest Network
If you have visitors who need access to your Wi-Fi, consider setting up a separate guest network. This keeps your main network secured while allowing guests to connect without compromising your personal devices. Make sure this guest network also has a strong password.
Regularly Update Your Router’s Firmware
Router manufacturers often release firmware updates to address security vulnerabilities. Regularly check for and apply updates to ensure your network is protected against the latest threats. This is an easy yet effective way to secure your home network.
Monitor Connected Devices
Keep track of devices that are connected to your network. Most routers have an interface that shows you a list of connected devices. If you notice any unfamiliar devices, take steps to remove them and change your password.
In addition to these tips, consider using a firewall and antivirus software to add extra layers of protection to your home network. Monitoring your network for unusual activity can also help you recognize potential threats before they become serious issues.
The significance of regular software updates
The significance of regular software updates cannot be overlooked when it comes to maintaining your cybersecurity. Software updates often include important fixes and improvements that help protect your devices from vulnerabilities. Staying current with updates ensures that your software can defend against the latest threats.
Why Updates Are Important
Every time software updates are released, they often include security patches that address known vulnerabilities. Cybercriminals frequently exploit these weaknesses to gain unauthorized access to systems and data. Regularly applying updates can help prevent malicious attacks that could compromise your personal or organizational information.
Benefits of Keeping Software Updated
Besides enhanced security, keeping your software updated comes with several benefits. Some of these include:
-
🚀 Improved Performance: Updates can boost the overall performance of applications and systems, making them run more efficiently.
-
✨ New Features: Many updates introduce new functionalities, which can enhance user experience and productivity.
-
🐞 Bug Fixes: Software updates often resolve bugs or issues that affect usability, leading to a smoother experience.
Companies frequently release updates to fix issues, so it’s essential to enable automatic updates if available. This way, your software will remain current without continual manual checks.
How to Manage Software Updates
To effectively manage your software updates, it helps to have a system in place. First, regularly check for updates on all your devices, including computers, smartphones, and tablets. You can also set reminders for critical software, such as your operating system and antivirus programs, to ensure you don’t miss important updates.
Make it a habit to monitor the software’s official website or settings for any alerts related to updates. In addition, using tools designed to check and automate updates can significantly simplify this process.
Overall, regular software updates are a key component of a strong cybersecurity strategy. By prioritizing updates, you can better protect yourself against cyber threats and enhance the functionality of your devices.
What to do if you fall victim to a cyber attack

If you fall victim to a cyber attack, it is crucial to act quickly and efficiently to minimize damage. Understanding the steps to take can help you regain control of your systems and protect your information.
Assess the Situation
First, identify the type of attack you are facing. Is it a malware infection, a phishing scam, or a ransomware attack? Understanding the nature of the cyber attack can guide your response. Disconnect your device from the internet to prevent further damage and stop any potential data theft.
Change Your Passwords
If you suspect that your accounts may have been compromised, change your passwords immediately. Use strong, unique passwords for each account. Consider using a password manager to help you create and store complex passwords securely.
Notify Relevant Parties
If the attack impacts sensitive information or involves financial transactions, notify relevant parties such as your bank, credit card company, and any affected services. Reporting the incident can help them take the necessary actions to protect your accounts.
Run Antivirus and Malware Scans
Perform a thorough scan of your device using reliable antivirus and anti-malware software. This can help identify and remove any malicious software that may have been installed during the attack.
Restore from Backup
If you have backups of your important files, you can restore them after ensuring your system is clean. Regularly backing up your data can be lifesaving in the event of a cyber attack.
Additionally, learn from the incident by reviewing how the attack occurred. Take steps to enhance your security measures to prevent future incidents. This might include updating your software, improving your email security, and educating yourself about recognizing cyber threats.
FAQ – Frequently Asked Questions about Cybersecurity Fundamentals
What should I do immediately if I suspect a cyber attack?
If you suspect a cyber attack, disconnect your device from the internet and assess the type of attack. Change your passwords and notify relevant parties.
How can I improve cybersecurity at home?
Improving home cybersecurity involves using strong passwords, enabling two-factor authentication, and keeping your software updated.
Why is it important to regularly update software?
Regularly updating software is crucial as it addresses security vulnerabilities and enhances performance, protecting your systems from potential threats.
What are some signs of a phishing attack?
Signs of a phishing attack include unexpected emails asking for personal information, generic greetings, and suspicious links. Always verify the source.





